Conducting a Business Continuity Risk Assessment
The risk assessment focuses on the risks that are associated with a resource, and then links these risks to an activity that uses these resources. This allows a risk to be raised against a single resource but for it to map onto all of the activities that use it, which reduces the repeating of information.
Multiple risk assessments can be created and managed within Abriska. To allow groups of resources to be included within risk assessments, the concept of an “Assessment” is used. An “Assessment” is a risk assessment conducted against one or more groups of assets. For example, this could be all resources from a single site, all resources which are used by a specific activity, or just all resources that a are part of a single contact.
To view the organisation's risk assessments, click on “Assessments” from the organisation homepage. To modify the name, description, or to assign this assessment to a contact, click on the assessment name and then click “Setup Assessment”.
Multiple module users
Users that have the Abriska 22301 and Abriska 27001 Information Security Management modules an additional risk assessment does not need to be completed.If a risk assessment has already been completed for the information security module of Abriska it only needs to be edited. You can view the information security risk assessment process here Information Risk Assessment Process Overview. The required editing is to the Vulnerability section of the assessment workflow. You can follow how to add this below. Please also see the risk assessment process videos here Risk Assessment Video Guides.
Risk Assessment Flow
Abriska guides the users through an organisation defined workflow that meets the requirements of ISO 22301. The default workflow is shown below.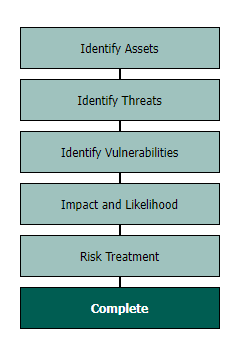
The links available on the sidebar will increase depending on the work stage.
Link Resources
Resources (assets) need to be allocated to each assessment to perform a risk assessment. Resources can be allocated to more than one assessment to allow central resources to be included throughout organisation risk assessments. To select resources for an assessment, click “View Resources” after clicking the assessment name. All available resources will be displayed with a filter to allow resources to be filtered by division. Select those that need to be included within this risk assessment by clicking the checkbox next to each resource name.Threat Identification
To enforce a level of consistency across each risk assessment that is conducted using Abriska, the same organisation threats list is considered each time. If one of the Organisational Threats is not applicable to a risk assessment (either it is outside of the scope of the assets/resources within the review or it is not a realistic threat) it can be excluded from the assessment. To exclude a threat, a justification must be provided.If a threat is outside those that are linked to a resource associated with this assessment, a default justification will be entered into these threats. If a threat is added that is not linked to any of the resources (see Threat to resource mapping), the threat will be highlighted red, as will the flowchart stage.
Identify Vulnerabilties
Individual vulnerabilities need to be identified that might increase the organisation’s exposure to certain threats. Click here for more information on setting up vulnerabilities and vulnerability types.Linking vulnerabilities to resources
Each vulnerability needs to be linked to at least one resource. This is achieved via a hierarchy of assets that are linked to this assessment. Resources are linked to each vulnerability via the “Resources” tabLinking vulnerabilities to threats
Each vulnerability needs to be linked to at least one threat. This is achieved by selecting from those threats that are applicable to this assessment. Threats are linked to each vulnerability under the “Threats” tab.Impact and Likelihood
For every threat that is applicable to the assessment, each of the risk variables and the duration (if applicable) need to be evaluated. From the main assessment screen, click on the “Impact and Likelihood” link to view the threat list. Each threat must be evaluated singularly by clicking on the threat name which will display the threat risk form.Each of the resources that are linked to this threat will be displayed on the “Resources” tab. For each of the risk variables specified, a tab will appear that allows each of the variables to be quantified. A red indicator on the tab shows that the section is unanswered which changes to green once this is answered. For each of the variables selected, identify the value that best fits with this threat. When considering the likelihood and impact of the threat, take into account the vulnerabilities that are also attached to that threat.
Risk Treatment
When the risk register has been created the vulnerabilities will have their risk score associated, treatment and actions can then be assigned to any vulnerabilities. These will also show within the Risk Actions page under the 'Organisation' tab on the main dashboard.Quantifying a vulnerability
If the threat that is being reviewed has any vulnerabilities related to it, an additional tab will display - “Vulnerabilities”. This tab will show all of the vulnerabilities within an expanding list. This allows an organisation to alter how a particular threat relates to a certain resource.Addressing a vulnerability
When a specific vulnerability is addressed by an organisation, it could be that a control has been put in place to mitigate the effect of a vulnerability, or because working practices have been changed. Select a vulnerability that has been addressed and click “End Date Vulnerability”. This allows a justification to be provided and the vulnerability will no longer be visible within the vulnerability list.Return to Risk Assessment or return to Main Page
