Information Risk Assessment Process Overview
For a full breakdown of the methodology within Abriska please refer to the Information Security Methodology. To undertake an ISO 27001:2022 compliant risk assessment within Abriska the following phases must be completed:
Identify Information and Information Processing Facilities
- Identify information and supporting assets/ information processing facilities
- Relate information to supporting assets so that once attributes have been assigned to information they will be inherited by the linked supporting assets. How this is done is explained here
- For each information assets assign attribute values for confidentiality, integrity and availability. This is done from the Assets screen and achieved by updating the 'Assets Attribute' (the attribute descriptions are default values but can be amended as required from within Organisation > Org. Setup > Assets Attributes)
Identify and Evaluate the Controls
- Within Abriska control maturity can be assessed for each Division that has been created within an organisation. However, the default position is that all of the divisions that are below the top level division naturally inherit the maturity of controls from the top level division unless the organisation decides otherwise.
- Control maturity inheritance or assigning to a lower level division is outlined separately in this guide.
- The first task when considering controls is to determine which controls are applicable and determine appropriate owners of controls.
- It is the necessary to assess the maturity of the applicable controls which is done from Control Maturity Assessment>Control Maturity Overview.
- For each control assign a maturity level by selecting the appropriate radio button on the control’s page. A description must be entered of mow the control is implemented and this description should support the assigned maturity level.
- In addition, a Recommended Improvement must also be entered. If the control maturity is acceptable at its current level, then this should be reflected as the recommended level with the appropriate radio button selected.
- The ‘Documents’ tab on the control screen provides the facility to attach any relevant documents that are referred to in the current level description e.g. policy documents. Adding documents is explained in the Organisation Setup section of this user guide.
Identify and Evaluate the Threats and Vulnerabilities
- First, the assessment that relates to the scope of the risk assessment needs to be created and set up in Abriska. Once set up the assets should be associated with the assessment. You can find the details of creating an assessment here Risk Assessment Video Guides.
- Once the assets are selected, an option to 'Default Threats' will appear; this will result in threats being linked to the assessment based on the asset types that are selected as being within the scope.
- The list of threats that are linked may include some that are not appropriate to the type of risk assessment being completed; therefore, from the list of threats that is presented when selecting the ‘View Applicable Threats’ option from the assessment workflow, those that are not appropriate to the scope and type of risk assessment can be deselected. To do this, select the threat and uncheck the ‘Applicable’ checkbox. Text should also be entered in the ‘Justification’ box to support the de selection.
- There are three components to a risk assessment that are applied to every threat/resource combination. By default these are impact, probability and vulnerability (however this terminology and methodology can be customised by the organisation).
- Vulnerability: Threats are linked by default to controls, which is used to calculate the resulting vulnerability score.
- Impact: the consequence of each threat must be evaluated to determine how each threat affects confidentiality, integrity and availability. A total score of 100 must be shared between these three attributes.
- Probability: The criteria to be used in the assessment are included in Abriska, but can be changed if required. The threat probability should be assessed ignoring any controls that are in place as far as possible (the effect of controls is taken into account in the vulnerability score, so would be ‘double counted’ if taken into account at this stage).
- Finally, additional specific vulnerabilities or weaknesses can be added on the ‘Identify Vulnerabilities’ screen in the assessment workflow. There is a library of vulnerabilities to choose from, or a different one can be added. These additional vulnerabilities may be an exception to a control implementation. Further information can be found here: Vulnerabilities.
Threat Probability Assessment
Within the Impact and Likelihood section, you go into each threat to assess its probability. This score is based on the probability of the threat occurring without any controls in place. Threat > likelihood dropdown > probability > select a level and provide a justification for future reference. The impact levels and descriptions can be edited. Please speak with support or an account manager.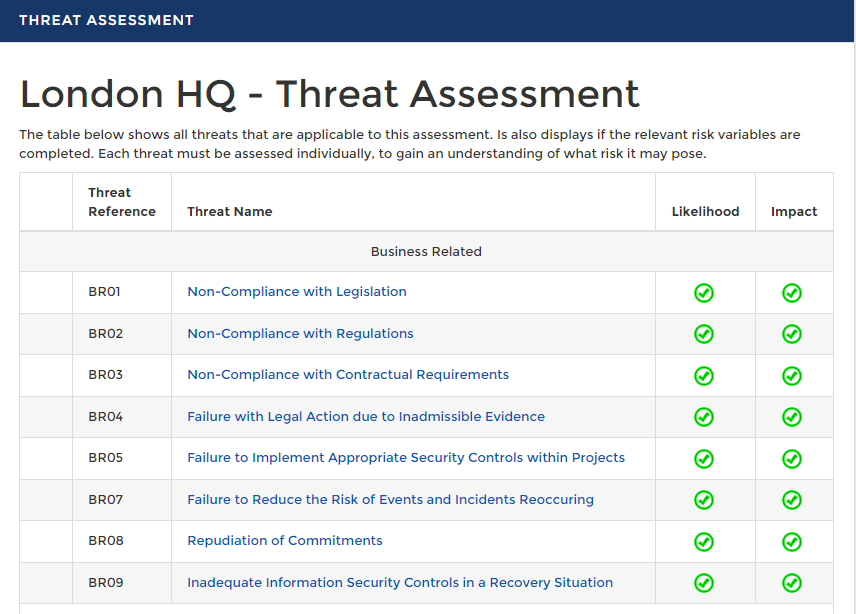
Completion and Outputs
Risk Assessment Video Guides for risk assessment process in Abriska. The risk assessment can be completed when all of the above processes have been completed. To generate your risks go to 'Risk Assessment' > Assessments > New Assessment > you will be presented with a workflow > Identify you assets for this assessment > this will automatically pull through the linked threats but you can edit this > identify additional vulnerabilities (see below) > Impact and Likelihood > here the probability assessment is completed on your threats (more detail below) > when both columns are displaying green ticks against all threats > 'Return to Assessment' > click into the 'Risk Reporting' dropdown > Risk Register > you will need to 'Generate Risks' ensure you tick 'Overwrite risk statements' > it will take 30-90 seconds for the risks to be generated.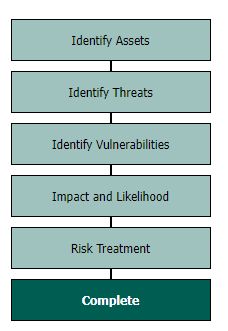
For more details on the risk calculation methodology please see Information Security Variables.
Risk Treatment
This section of the assessment workflow leads into the treatment of risks associated to vulnerabilities if any have been added. The vulnerabilities will have an associated risk score once the risk register has been generated and they too need to go through the treatment and action process. Address specific vulnerabilities to reduce the risk of threats occurring. Vulnerabilities and their actions can also be access via the Risk Actions page from the Organisation tab off of the main dashboard.
Risk Register
The risks are broken down by the threat most prominent and the statement will highlight the threat, key assets impacts and key controls. In Abriska the status panel will provide filer options and indicators of items that need reviewing or completing.Risk Score Matrix
In Abriska on the risk register this tab will allow you to view your absolute, current and treated risks. The Risk Score Matrix report is an Excel workbook that comprises a range of individual spreadsheets. The first spreadsheet provides a list of all resources and the threats that they are attached to along with the risk score that relates to the resource threat combination. Each resource is allocated a reference number and that number relates to a separate sheet within the workbook, one sheet (tab) for each resource. This tab shows the detail of the impact (C, I and A) and all of the threats attached to the resource along with the relevant scores.Risk Treatment Plan
The Risk Treatment Plan (RTP) is an Excel spreadsheet that presents all of the controls that are applicable to the risk assessment. It shows the current implementation status of the control and the recommended action to improve the maturity level (if appropriate). It also shows that threats that the control is linked with. It shows the highest risk levels that from the linked threats, with scores shown as what the risk would be without the control, the current level according to the control maturity and, if appropriate, the level that would be attained if the control maturity level were increased as recommended. The other information in the RTP is derived from the ‘Control Risk Strategies’ option. The use of this option is described in the section on risk treatment.Organisation > Control Maturity Assessment > Control Maturity Overview > Division > Control Applicability and Owners
See Risk Assessment Video Guides for a 7 part video series on the above steps.
Return to Risk Assessment or return to Main Page
